2021-12-21 00:34:0 Author: www.sentinelone.com(查看原文) 阅读量:23 收藏
The primary objective in information security is to reduce the risk exposed through cyber threats towards an organization. To achieve that, security leaders aim to make informed decisions that allow their organization to best protect, detect, respond, and recover from cyber threats. Therefore, when looking into reducing risk, security leaders often choose to reduce significant dependencies in their enterprise architecture and procedures towards a particular vendor or capability.
That strategy makes good sense, but what about when you are considering security software? Some believe that OS vendor-supplied security software must be “safer” or less risky than that of 3rd party vendors. After all, this line of thinking goes, who knows the OS better than those who developed it?
Yet choosing security software sold by your operating system vendor increases your dependency on a single vendor, and in some of the most security-critical areas, too. In this post, we’ll review the pros and cons of relying on your OS vendor for security software, and we’ll take a look at what 3rd party vendors offer that an OS vendor cannot.

Security and Operating Systems | Expertise Matters
It goes without saying that the developer of any software knows that software best – they are after all, the owners of the source code – but we are where we are in cybersecurity in no small part because developers frequently fail to understand the security implications of their own products.
Responsible software companies implement bug bounty programs to invite external security specialists to audit their software, and this is no less true of OS vendors like Microsoft, Google, Apple and Red Hat Linux as it is of developers of browsers, and indeed, security software vendors, too. The more complex a piece of software, the more likely there are to be vulnerabilities, a fact borne out by recent CVE statistics in Microsoft Windows, for example.
- In 2020, Microsoft confirmed 1,220 new vulnerabilities impacting their products, a 60% increase on the previous year.
- 807 of 1,220 vulnerabilities were associated with Windows 10, with 107 of those related to code execution, 105 to overflows, 99 to gaining information, and 74 to gain privileges.
- In 2021, 836 new vulnerabilities have been confirmed so far, 455 of which impact Windows 10 and 107 allow malicious code execution.
While this data refers to the most recent vulnerabilities, it’s also important to understand that many old vulnerabilities are still actively exploited by threat actors.
Operating system software is, and always will be, riddled with security vulnerabilities. Across Microsoft products, it is the Windows operating system where most security bugs are being found. Additionally, Microsoft has the highest rate of zero days compared to any other operating system vendor. Even more alarming is that most of these vulnerabilities relate to elevation of privilege or remote code execution: high risk vulnerabilities that threat actors can and do use to compromise organizations.
When a vendor is dealing with such an overwhelming amount of CVEs affecting so many different product lines, increasing your dependency on more products from that vendor requires a moment’s thought.
How much time and effort can the OS vendor extend to ensuring vulnerabilities in their security software offering are found and dealt with in a timely manner? A 3rd party vendor with a much smaller portfolio and expertise in security itself may be much-better placed to provide a reliable and effective security solution than an OS vendor with other priorities.
Moreover, with such a huge code base containing potentially vulnerable code, code dependencies in OS vendor products can present attackers with unexpected opportunities. For example, in 2021 SentinelLabs discovered a simple privilege escalation bug in Windows Defender that had been in the code since 2009.
CVE-2021-24092: 12 Years in Hiding
A Privilege Escalation Vulnerability in Windows Defender
As we have seen, just because an OS vendor knows their own product better than anyone else, it doesn’t follow that they are best placed to understand or even deal with the security implications of that software. And the bigger and more complex the software, the more true that is going to be.
When you add all this together, it raises a troubling thought: is the vendor that is likely the source of the most vulnerabilities in your environment really the vendor you want to select for cybersecurity?
Nonetheless, perhaps there is another good argument for preferring security software from an OS vendor rather than a dedicated security solutions specialist: If one were looking for a turnkey solution, perhaps the OS vendor’s own security offering should be less hassle than installing a security solution from a third party vendor?
There are a number of issues to consider here; installation, licensing, cost, ease-of-use, integration, and, ultimately, the effectiveness of the protection.
E5 Licensing Complexities | What’s Not Included In The Box
Among the major OS vendors, Microsoft is unique in having chosen to develop and sell a product to protect its own operating system software. Arguably, there is a conflict of interest in a software company looking to build revenue by marketing a security product to protect its other products, and potential customers might wonder whether the engineering effort expended there would have been better spent on directly securing those products.
Even if organizations choose to pay the premium and procure Microsoft 365 E5 Security, Enterprise Mobility and Security E5, or Windows E5 licenses, they often discover after the fact that they end up requiring additional 3rd-party products to cover the gaps of Microsoft’s security portfolio:
- When it comes to Extended Detection Response (XDR) solutions, the general consensus in the industry is that a solution must be able to perform 3rd-party data ingestion to perform cross-workload data analytics and response actions. Microsoft 365 Defender lacks the ability for 3rd-party data ingestion, so organizations are left with a technology that can only process its own dataset and therefore only protect the limited scope of Microsoft solutions.
- Microsoft’s Endpoint Platform Protection (EPP) and Endpoint Detection Response (EDR) offering is called Microsoft Defender for Endpoint. The solution continues to lack in several critical areas including detection quality, automatic remediation of cyber threats on non-Windows 10 endpoints, and 1-click recovery from cyber threats.
Many customers evaluating Microsoft alongside SentinelOne consistently say that the “With E5 you have everything you need” claim of Microsoft turned out to be inaccurate. Once they began their evaluations, the gaps became significant, and over time compounded by the fact that Microsoft tends to introduce additional niche products.
For example, Microsoft recently made the decision not to support Kubernetes clusters and containers with Microsoft Defender for Endpoint; instead, they announced Microsoft Defender for Containers, yet another product which is not included in E5 and which again requires additional licenses, procurement, and deployment.
Beyond that, the procurement process can quickly become very complex as all the different products are spread across dozens of different licensing models in Microsoft Azure, Microsoft Windows, and Microsoft 365.
Some of these licensing models are per endpoint, others per user, and still others are pay-as-you-go. This plethora of offerings can make it extremely difficult to predict the actual cost of the platform for a business with multiple, complex needs.
In contrast, a solution like the Singularity platform has a very simple, straightforward licensing model where customers can choose between:
- Singularity Core – On-device, NGAV with autonomous behavioral AI that does not rely on the cloud to detect, prevent and remediate file-based and fileless attacks, including ransomware.
- Singularity Control – Singularity Core with additional endpoint control capabilities like firewall, device control, and more.
- Singularity Complete – Singularity Control with additional Endpoint Detection Response (EDR), Cloud Workload Security, and Network Security capabilities.
All three options are licensed in a subscription model per agent/month, with no hidden costs.
Ease of Use and Integration
It’s a natural and expected consequence of using software from one vendor that, where they have other offerings, they will try to encourage take up of their other products. But one of the most important things for an enterprise when choosing security software is how it can reduce risk, decrease dependencies, and easily integrate with the rest of the security stack.
With Singularity XDR, organizations are able to gain unified visibility across their technology ecosystem, and benefit from unparalleled data analytics with centralized cross-workload response actions.
With this approach, SentinelOne customers have the flexibility they need in order to choose a best-of-breed strategy while being able to centralize into a unified security platform.
In contrast, Microsoft’s methodology pushes organizations into a closed ecosystem, which means increasing the dependency to a single vendor that can quickly become a single point of failure.
The Ultimate Test: Who Protects Best?
Every vendor will tell you they are better than the competition, and it’s vital for security leaders to look at independent 3rd-party evaluation like when comparing security products.
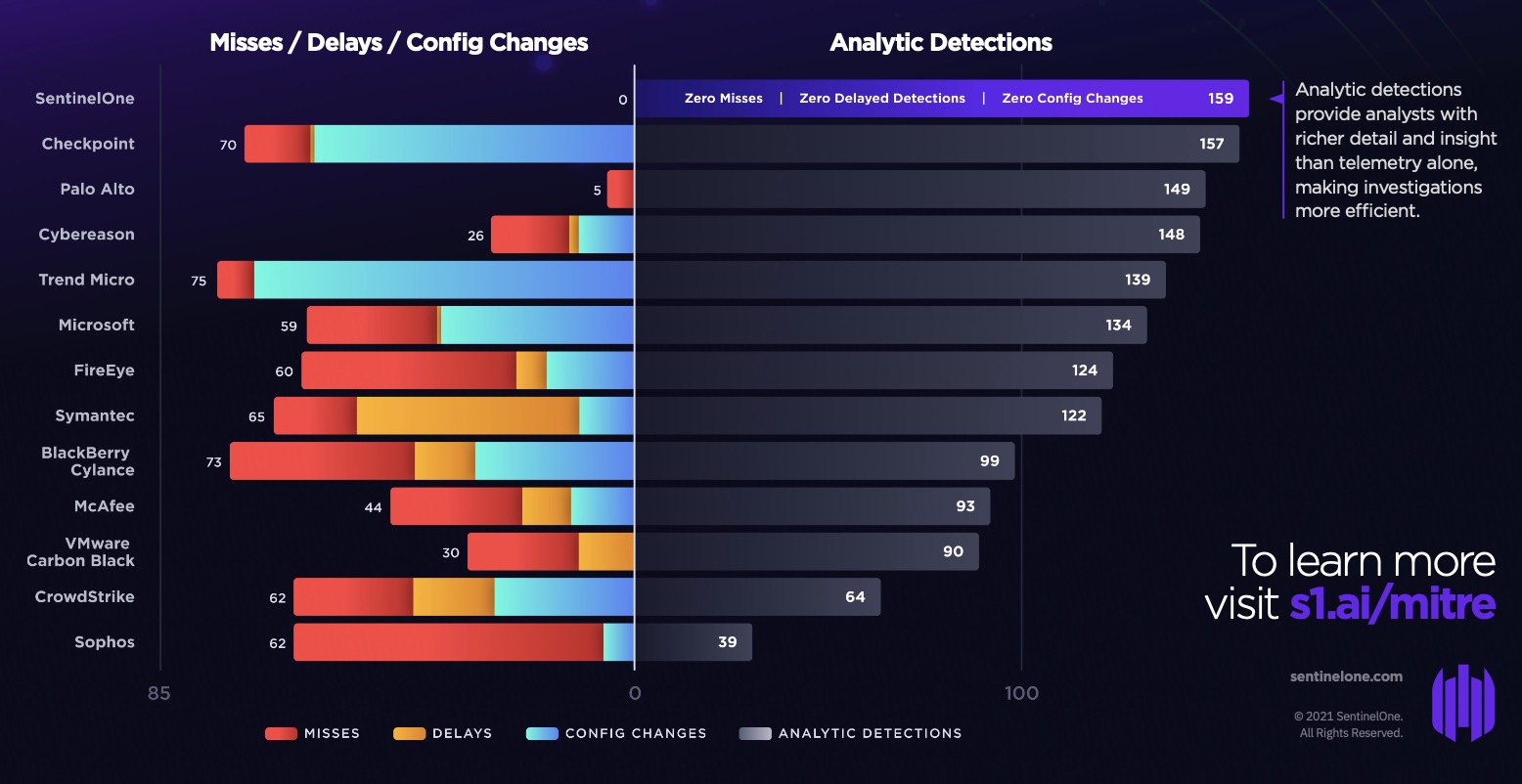
The most recent MITRE Engenuity ATT&CK Evaluation is a good place to start.
Despite the fact that the simulation took place predominantly on Windows, Microsoft’s own security product still had 23 missed detections. During the test, they paused the evaluation 35 times to perform configuration changes, including for their detection logics: a luxury an organization does not have in the real-world during a cyber-attack.
In comparison, SentinelOne had zero misses, zero configuration changes, and 100% visibility.
Taking Advantage of a Best-of-Breed Approach
Security leaders aware of the pitfalls we’ve mentioned above are choosing a best-of-breed approach and bringing in security-first vendors to partner with for their security requirements.
With Singularity, SentinelOne provides a best-in-class Extended Detection Response (XDR) platform that extends protection from the endpoint to beyond with visibility, proven protection, and unparalleled response:
- One security console: Built for centralized & intuitive operations. Whether SOC analysts are chasing bad actors or security administrators need to configure device control policies, all can be achieved in one console.
- Best-in-class EPP + EDR for modern threats: Every endpoint is equipped to prevent and detect with robust static & behavioral AI, even when offline.
- Consistency: SentinelOne provides you consistency in terms of what features are available and ensures feature parity across Windows, macOS, and Linux.
- Time-saving automation: Automatic attack reconstruction with Storyline™ technology, autonomous & 1-click remediation and patented rollback, dedicated in-house experts for MDR, DFIR, and threat hunting
SentinelOne Singularity XDR
See how SentinelOne XDR provides end-to-end enterprise visibility, powerful analytics, and automated response across your complete technology stack.
Conclusion
Cybersecurity is all about managing risk as effectively as possible. There is no organization in the world that is immune to cyber threats. Over the years, security leaders have been required to make a choice between best-of-suite or best-of-breed approaches for their technology stack.
With the increasing complexity of cyber threats, the continuous increase of cyberattacks, and the increased dependency on operating system vendors, organizations are looking to partner with security-first companies that can provide a holistic approach to security.
If you would like to learn more about how SentinelOne can reduce cyber risk across your entire organization – Windows, Linux, macOS, IoT, mobile and cloud workloads – contact us or request a free demo.
如有侵权请联系:admin#unsafe.sh
