If you run Java applications in containers, then it is critical that you check for Log4Shell vulnerabilities, given the high severity of this potential exploit. Qualys Container Security offers multiple methods to help you detect Log4Shell in your container environment. The Container Security sensor checks both running containers and container images for the following vulnerabilities:
- QID 376157/CVE-2021-44228 – Detect venerable log4 jar for versions at or below 2.14
- QID 376178/CVE-2021-45046 – Detect venerable log4 jar for versions at or below 2.15
- QID 376194/CVE-2021-45105 – Detect venerable log4 jar for versions at or below 2.16
Qualys highly recommends running a vulnerability scan against all your running containers because Java applications running the container are susceptible to Log4Shell vulnerability exploits. To detect vulnerabilities in running containers, you must deploy the Container Security sensor in “General” mode on the hosts running the containers. The sensor will scan each running container on the host looking for a running Java process, and then check whether that process has the log4j jar file loaded. If the log4j jar is loaded, it will check for the version of the log4j and, if it is venerable, it will report it.
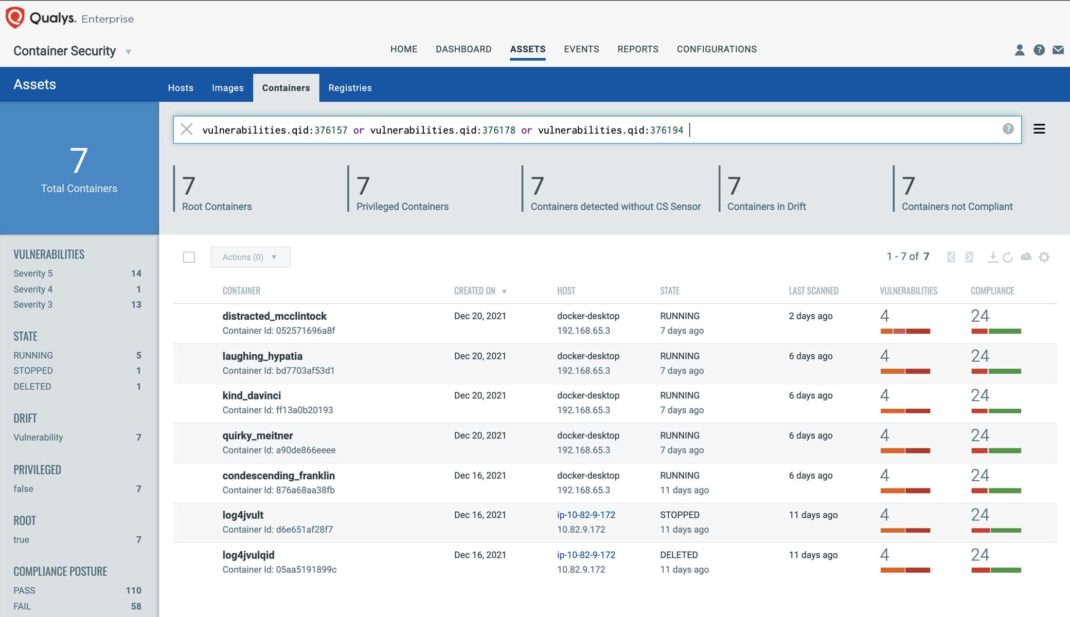
To see all the containers impacted by these vulnerabilities, navigate to the “Container Security” application, then select the “Assets-> Container” tab, and use the following QQL query:
vulnerabilities.qid:376157 or vulnerabilities.qid:376178 or vulnerabilities.qid:376194

To view details of the vulnerability, you can click on the vulnerable container and navigate to the “Vulnerabilities” tab as shown in the screenshot below:

In addition to scanning running containers, Qualys recommends that you scan container images for Log4Shell vulnerabilities.
Catching and remediating Log4Shell vulnerabilities in container images will eliminate exposure to the vulnerabilities when the image is instantiated as a container. To detect Log4Shell vulnerabilities in container images, you will need to run the Container Security sensor version 1.10.1 or greater in any of the supported modes. The Container Security sensor will look for all the jar files in the image, searching for the log4j jar. If the log4j jar is not in the list of the jar files, it will then look inside each of the jar files. If it detects a vulnerable version, then it will report any/all instances.
To view all the impacted images, navigate to the Qualys Container Security app, then select the “Assets-> Images” tab, and use the following QQL query:
vulnerabilities.qid:376157 or vulnerabilities.qid:376178 or vulnerabilities.qid:376194

To view details of the vulnerability, you can click on the image and navigate to the “Vulnerabilities” tab as shown in the screenshot below:

Qualys Container Security offers a comprehensive solution for detecting vulnerabilities, including Log4Shell, across the entire lifecycle of the container from build time to runtime. Check back periodically to our Log4Shell Resources page for the latest threat intelligence for container security.